How To Restrict Event Hub Public Network Access via Azure Policy
Yesterday I published a policy definition to restrict Event Hub public network access. After reading my blog post, my friend and colleague Ahmad Abdalla told me there is a gap in my policy definition. Although once assigned, the policy will deny the creation of a NEW Event Hub namespaces with public network access enabled, but if you are enabling public network access on an EXISTING Event Hub namespace via the Azure portal, the policy does not deny the operation.
After some investigation, I found that in the Activity Log that my update on the Azure portal was actually targeted the Microsoft.EventHub/Namespace/NetworkRuleSets instead of the Microsoft.EventHub/Namespace resource type.
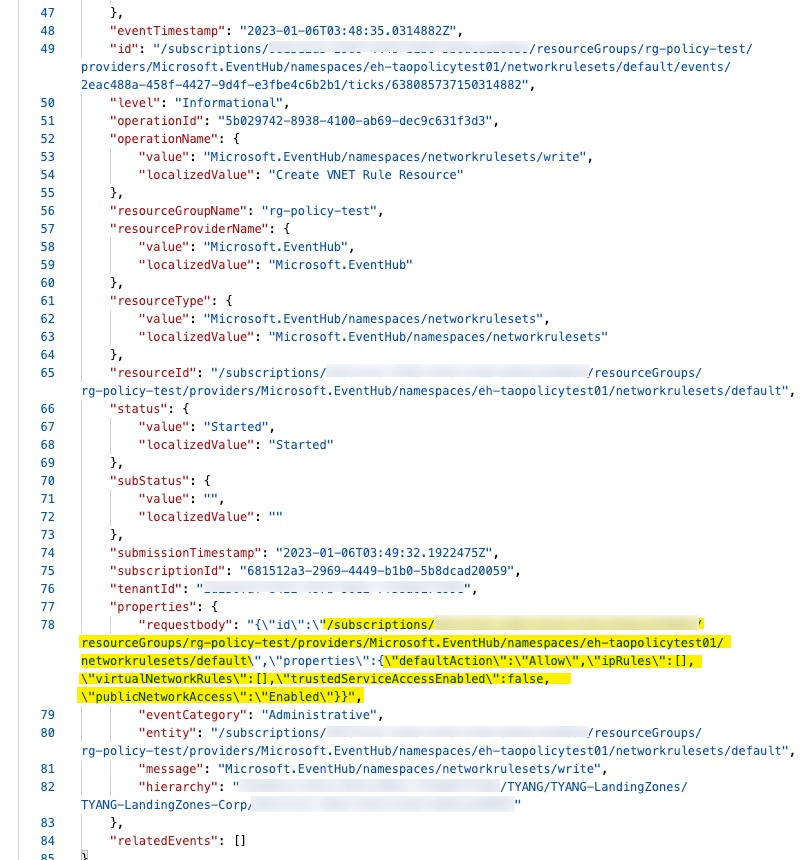
After the successful operation, the property Microsoft.EventHub/Namespace/publicNetworkAccess was set to Enabled and policy did not block it.
In order to cater for this behaviour, I had to create an additional policy definition targeting the Microsoft.EventHub/Namespace/NetworkRuleSets resource type. The policy definition is available in my Azure Policy GitHub Repo.
In Summary, to completely restrict public network access for Event Hub, you need to assign both policies:
- Azure Event Hub namespaces should disable public network access
- Azure Event Hub Namespace Network Rule Set should disable public network access
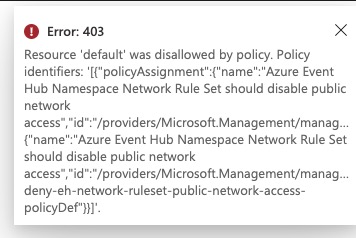
Once both policies are assigned, I was able to fill the gap of updating the existing Event Hub namespace via the Azure portal. When I tried to enable public network access, the policy blocked the operation:

Leave a comment